Subscribe
Sign up for timely perspectives delivered to your inbox.

Data security is a large and impactful social issue. The Global Technology Leaders Team examines the rising threat landscape and the cybersecurity industry’s solutions to this global challenge.
Data security is gaining importance among consumers, businesses and governments and is increasingly an attractive investment theme, as it plays an essential role in protecting consumer identities, corporate data and geopolitical stability. The global cost of cybercrime is estimated to reach $6 trillion in 2021, rising to $10.5 trillion in 2025, having grown at a compound annualised growth rate (CAGR) of 15% from 2015 to 2021*. This strong growth can in part be attributed to the frequency and intensity of attacks that have increased since the beginning of the pandemic as a result of the accelerated shift to working from home and the increasing reliance on digital interactions.
SolarWinds is a major software company based in Oklahoma, which provides network and infrastructure monitoring to a multitude of organisations globally. In December 2020, a large-scale breach was discovered that hit the company’s Orion network monitoring software, which had 33,000 customers across the public and private sector. The SolarWinds breach was an example of hacker innovation and triggered a supply chain incident as it exposed new vulnerabilities across corporate and government entities. It relied on tactics designed to evade many of the security tools and protocols in use.
The breach was also a sign of increasing boldness by these threat actors, and subsequent incidents reported in the press brought attention to increased efforts to compromise security software vendors themselves, and the vulnerability of critical infrastructure, such as municipal water systems.

The threat landscape has evolved as ransomware attacks have become easier to perpetrate as identified network vulnerabilities and breach software can now be purchased from other cyber criminals and cryptocurrencies have also created an anonymous way to receive payments. This backdrop has created an inflection of demand for security software tools and has placed greater pressure on IT managers, senior executives and corporate directors to not only ensure that security tools are purchased to cover vulnerabilities across their IT architecture, but that the tools purchased are truly effective and able to evolve with the threat landscape.
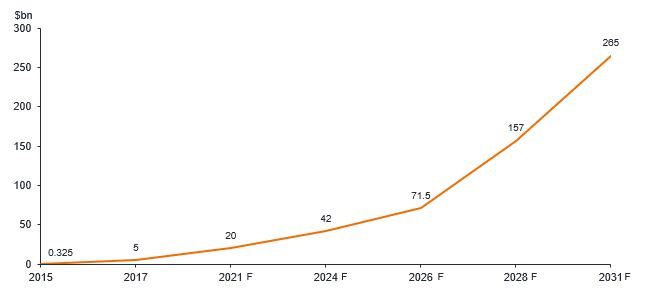
We expect the threat landscape to continue to evolve, as many of the themes and drivers that existed coming into 2021 remain in place today. Although difficult to measure with precision, the growth rate of the cost of cybercrime has definitively outpaced the growth of expenditure on security software in recent years and this is likely to continue going forward. Cybersecurity Ventures estimates that the cost of ransomware attacks alone will reach US$265 billion by 2031.
In response to this worsening threat landscape, security buyers are focusing more on the efficacy of tools purchased. Cybersecurity companies themselves recognise the increased role they need to play, evidenced by “resilience” being chosen as the headline theme of this year’s RSA conference (RSA is the market leader for cybersecurity and digital risk management solutions). This reflects the cybersecurity industry’s goal for companies to experience fewer breaches and for any breach to be withstood. Companies are increasingly implementing ‘zero trust’ frameworks, which call for isolation of failures through compartmentalisation of failure zones (eg. using network segmentation) and limiting trust to only the minimum permissions with respect to what is absolutely required to accomplish an activity within an IT network. The guiding principles for this concept are constant verification of user authentication or authorisation, least privileged access, and segmented access based on network, user, device, and app.
Looking forward, we see cybersecurity becoming more important in both public cloud environments and software supply chains, where recent breach activity has revealed vulnerabilities in infrastructure that has not historically been protected by third-party security tools. Economic models are still emerging as cybersecurity customers look to better understand value propositions and that lines of demarcation settle between third-party security vendors and public cloud and infrastructure software vendors. Given the scope and complexity of these IT environments, we expect significant pools of security spend to emerge in these two areas over time.
Among the cybersecurity specialist companies is CrowdStrike, which offers a differentiated platform protecting endpoints (both personal computers and servers) employing artificial intelligence-assisted threat graphs to prevent breaches. The company also shares information learned in one breach attempt with its entire network of customers. Tenable offers valuable scanning of IT infrastructure in the identification of breaches and vulnerabilities, while NortonLifelock is another key player in the protection of consumers from both malware and identity theft.
Tech giants also play an important role in securing IT infrastructure. Microsoft disclosed annual security business revenues of $10 billion (growth of 40% year-over-year) by protecting email, endpoints, identity, and other threat vectors, and Amazon, through its Amazon Web Services division, is securing workloads within its cloud infrastructure. Meanwhile, Alphabet recently committed to investing $10 billion into cybersecurity as part of President Biden’s cybersecurity directive. It has since made a series of product announcements aimed at improving the security of the Google Cloud Platform and Google Workspace productivity suite.
The cybersecurity industry is ever-changing in response to an evolving threat landscape. As the demand for the sector’s products and services increase, technology companies must come up with innovative solutions. This dynamic creates some interesting and potentially rewarding opportunities for investors. However, the increased demand for data security has also led to a rapid increase in valuations in some sub-segments of the sector, something that investors need to take into consideration.